The eResources Consortium was established in 2001 by the Australian members of NSLA.* In recent years, the Consortium has secured savings of over $1 million each year in licensing fees and during COVID-19 lockdowns negotiated vital remote access conditions. It keeps members informed of new products, implements value for money licenses and closely monitors usage to ensure the maximum reach for our collective users.
The Consortium engages with vendors and publishers to develop relationships that benefit all parties, maximising efficiency and value. It actively collaborates with many organisations that offer products and services to our community, including library product vendors, non-profit organisations and private companies.
The benefits of working with the NSLA eResources Consortium include that:
- it provides a single point of contact for communication, trials, invoicing, licensing, renewal, and administrative issues
- our members have a strong trust relationship with us, and value the information that we provide to them.
* While a member of NSLA, the National Library of New Zealand is not a member of the Consortium. The National Library of New Zealand is the lead agency of Electronic Purchasing in Collaboration (EPIC), New Zealand’s national consortium. The NSLA Consortium collaborates with EPIC and the CAUL Electronic Information Resources Consortium on areas of mutual interest.
Governance and management
The Consortium secretariat operates out of the National Library of Australia’s Collaboration Branch.
The Consortium Terms of Reference set out the purpose, objectives, governance, management and membership of the Consortium. They are reviewed annually with the Consortium Strategic Plan which sets out in more detail the agreed priority activities.
Working with us
The process
The Consortium Renewals Officer reviews all offers and is responsible for negotiations with vendors. Once an acceptable offer has been agreed upon in principle, the offer will be circulated to Consortium members. Subsequent negotiation may be required dependent on member responses. The Consortium Renewals Officer will coordinate member confirmations and inform vendors. The vendor will then invoice the Consortium.
Consortium member decision making processes vary and final acceptance of offers is dependent on the completion of those internal processes. In recognition of this, the request for renewal offers is extended in September for the following year.
Pricing models
The NSLA Consortium’s preferred pricing model is one based on either the number of concurrent users or on site licences, rather than population based. See the Consortium’s Statement of Principles Guiding Licence Negotiation. There are a number of different pricing models that are used by vendors when dealing with the Consortium. Our preferred model is based on a band structure where each member is classified based on an understanding of members’ budgets and the nature/type of library (e.g. research focus). This structure recognises the differences in the libraries and charges accordingly. Using the band structure below a vendor will price their product for the Consortium.
Band 1 – SLNSW, SLV and NLA
Band 2 – SLWA, SLQ
Band 3 – Tasmania, SLSA
Band 4 – ACT, LANT
Licence principles
Vendors’ licence agreements are assessed against the Consortium’s Statement of principles guiding licence negotiation. Copyright is a significant principle and the Consortium prefers that licences permit, at a minimum, use as allowed under Australian copyright law which includes unlimited viewing, and downloading and printing for permitted purposes of research or study.
Also included in the principles is the Consortium’s preference that licences permit the use of products for the purpose of responding to reference queries and to fulfil interlibrary loan requests from other libraries.
For further information on this, National and State Libraries Australasia and the Council of Australian University Librarians, created Joint Principles for Access to Electronic Resources.
Principles guiding licence negotiation
The Statement of principles guiding licence negotiation [PDF] sets out:
- Definition of users
- Required rights for access and use
- Archiving/preservation
- Pricing model
- Authentication
- Service and support levels
- Monitoring/user statistics
- Liabilities
- Privacy
- Administrative arrangements
Rights for access and use
Access
Flexible access is important and is essential service for users who may not be able to physically visit our libraries. Access should at a minimum include:
- access to products for individual ‘walk-in’ Users of Members
- remote access for registered users of Members
Registered members and conditions of access
Registration as a member of a NSLA library requires proof of identity and address/residence. Once registered the member is given a library card or account. Registration procedures are strictly implemented and are routinely audited.
Before a user can gain access to eresources they must first agree to the terms and conditions of access. The conditions of access specify that use must be for research and study purposes only and not for business, commercial or work-related purposes. The conditions of access also direct users to read any copyright or terms of use statements appearing within the eresource and act in accordance with instructions. Where no statement restricting copying is evident, users are obliged to comply with the Copyright Act 1968 (Cth).
Use
Any Licence entered into by the Members must recognise and should not restrict or abrogate the rights of the Members or their User community permitted under Australian copyright law, or comparable fair dealing provisions of the jurisdiction of the licence.
Remote Access
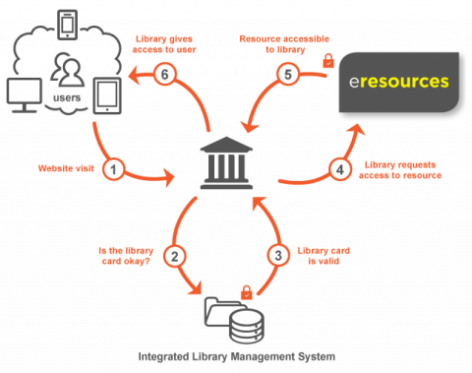
Remote access for registered library members is an essential service for users who may not be able to physically visit our libraries. Consortium members have well established protocols in place to provide remote access to our members. Once a user has a card and they wish to access eresources offsite they need to login with their card details. Consortium members use a combination of IP authentication and EZproxy to establish and authenticate the user’s credentials.
Remote access in detail
- Website visit: A client’s browser visits our e-resources management system (EZproxy), discoverable via a catalogue record, or the eresources page.
- Library card check: The EZproxy software requires that the user have valid credentials, either locally configured or verified against an external Integrated Library Management System (ILMS).
- HTTP request: EZproxy makes a standard HTTP request to the subscribed database, which is permitted by the provider as it originates from an IP address included in our subscription details.
- Standard response: The resource provider responds with the appropriate search results, documents or other data.
- Altered HTML response: The data returned by the provider is scanned by the EZproxy and is altered. Any links to example.com are changed to become example.com.rp.nla.gov.au. This provides a seamless experience to the end user and ensures that any links followed will be routed via the EZproxy software.
Notes
- The diagram and the explanation are to aid conceptual understanding, and are not a technical description of the authentication process.
- EZproxy is used very broadly in libraries, and is available from the OCLC.
Statistics
Usage statistics are important as they allow Consortium members to derive useful metrics such as cost-per-use; make better-informed purchasing decisions; and plan infrastructure more effectively. As a member of Counting Online Usage of Networked Electronic Resources (COUNTER), the Consortium’s preference is for vendors to provide COUNTER compliant usage statistics.
Partnerships and collaboration
The Consortium is a member of the International Coalition of Library Consortia (ICOLC) an informal group currently comprising approximately 200 library consortia from around the world. ICOLC supports participating consortia by facilitating discussion on issues of common interest.
As a member of COUNTER (Counting Online Usage of Networked Electronic Resources) the NSLA Consortium is part of an international initiative serving librarians, publishers and intermediaries by setting standards that facilitate the recording and reporting of online usage statistics in a consistent, credible and compatible way.
Contact
Convenor, NSLA eResources Consortium
c/- Collaboration Branch
National Library of Australia
Parkes Place
CANBERRA ACT 2600
phone: +61 (0) 2 6262 1785
email: nslaconsortium@nla.gov.au
Renewals
email: nslaconsortium@nla.gov.au (marked attention to Renewals Officer)
Consortium members
Library & Archives NT
Cathy Johnston, Manager Collection Management
phone: +61 (0) 8 8999 6983
email: Catherine.Johnston@nt.gov.au
Libraries ACT
Amy Chan, Assistant Director, Collections
phone: +61 (0) 2 6207 5446
email: amy.chan@act.gov.au
Libraries Tasmania
Ruth Snape, Librarian, Systems Support & Delivery
Phone: +61 (0) 3 6155 5565
email: ruth.snape@libraries.tas.gov.au
National Library of Australia
Libby Cass, Director, Curatorial & Collection Research
phone: +61 (0) 2 6262 1871
email: libby.cass@nla.gov.au
State Library of New South Wales
Sean Volke, Senior Librarian, Online Resources
phone: +61 (0) 2 9273 1639
email: sean.volke@sl.nsw.gov.au
State Library of Queensland
Rachel Wray, Team Leader, eResource Management
phone: +61 (0) 7 3840 7803
email: rachel.wray@slq.qld.gov.au
State Library of South Australia
Anthony Laube, Coordinator Collection Development (Published Collections)
phone: +61 (0) 8 7424 6176
email: Anthony.Laube@sa.gov.au
State Library Victoria
Paul Clerici and Vicki Nelson, Collection Development & Description
phone: +61 (0) 3 8664 7385
email: elacq@slv.vic.gov.au
State Library of Western Australia
Andrew Black, Collection Liaison, Acquisition and Description (Published materials)
phone: +61 (0) 8 9427 3442
email: andrew.black@slwa.wa.gov.au
Coenraad Brand, Collection Liaison, Acquisition and Description (Published materials)
phone: +61 (0) 8 9427 3487
email: coenraad.brand@slwa.wa.gov.au